In this chapter, we will learn about the important password cracking tools used in Kali Linux.
Hydra Hydra is a login cracker that supports many protocols to attack (Cisco AAA, Cisco auth, Cisco enable, CVS, FTP, HTTP(S)-FORM-GET, HTTP(S)-FORM-POST, HTTP(S)-GET, HTTP(S)-HEAD, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MySQL, NNTP, Oracle Listener, Oracle SID, PC-Anywhere, PC-NFS, POP3, PostgreSQL, RDP, Rexec, Rlogin, Rsh, SIP, SMB(NT), SMTP, SMTP Enum, SNMP v1+v2+v3, SOCKS5, SSH (v1 and v2), SSHKEY, Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP).
To open it, go to Applications → Password Attacks → Online Attacks → hydra.
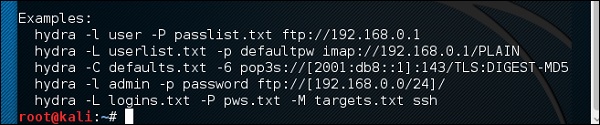
The terminal console will open, as shown in the following screenshot
. 
In this case, we are going to brute force metasploitable machine FTP service, which has IP 192.168.1.101
We have created in Kali a list of words with extension ‘lst’ in the path usr\share\wordlist\metasploit.
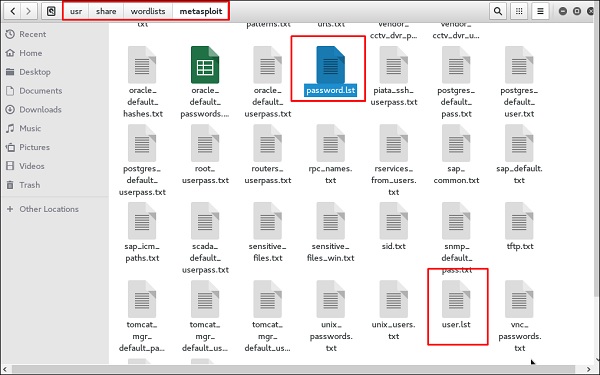
The command will be
as follows − hydra -l /usr/share/wordlists/metasploit/user -P /usr/share/wordlists/metasploit/ passwords ftp://192.168.1.101 -V where -V is the username and password while
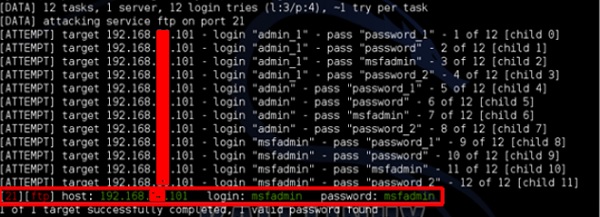
trying As shown in the following screenshot, the user name and password are found, which are msfadmin:msfadmin
 Johnny
Johnny
Johnny is a GUI for John the Ripper password cracking tool. Generally, it is used for weak passwords.
To open it, go to Applications → password attacks → johnny.
In this case, we will get the password of the Kali machine with
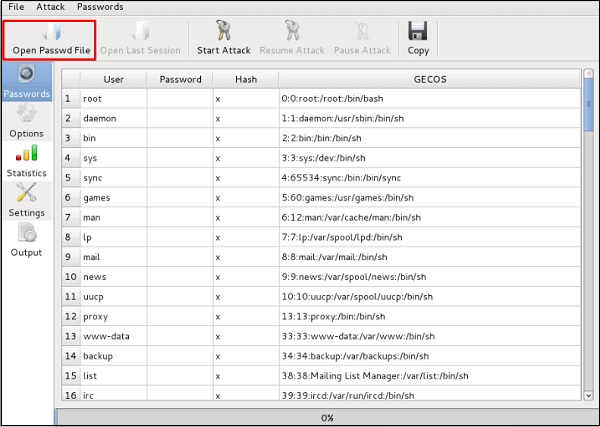
the following command and a file will be created on the desktop. Click “Open
Passwd File” → OK and all files will be displayed as in the following screenshot.
Click “Start Attack”.
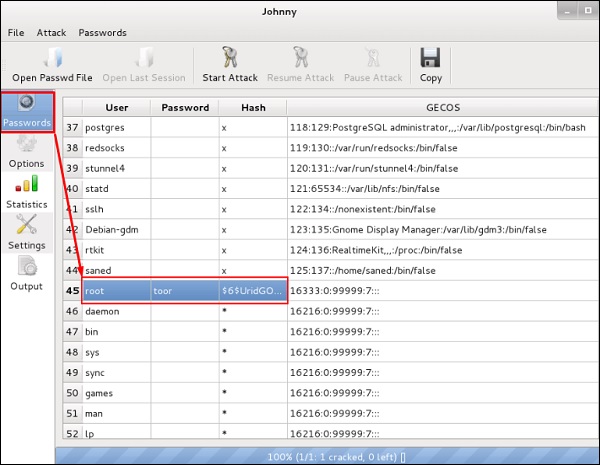
Once the attack is complete, click on “Passwords” in the left pane and the password will be disshadowed
. 
John
john is a command-line version of Johnny GUI. To start it, open Terminal and type “john”.
<img src="https://www.tutorialspoint.com/kali_linux/images/unshadowing.jpg" alt="Unshadowing" />
In case of undoing the password, we need to type the following command −
root@kali:~# unshadow passwd shadow > unshadowed.txt
Rainbowcrack RainbowCrack
software decrypts hashes by searching for rainbow tables. Rainbow tables are ordinary files stored on your hard drive. Generally, Rainbow tables are purchased online or can be compiled with different tools.
To open it, go to Applications → Password Attacks → click “rainbowcrack”.
The command to crack a hash password is −
rcrack path_to_rainbow_tables -f path_to_password_hash
SQLdict
is
a dictionary attack tool for SQL Server and is very easy and basic to use. To open it, open the terminal and type “sqldict”. The next view opens.
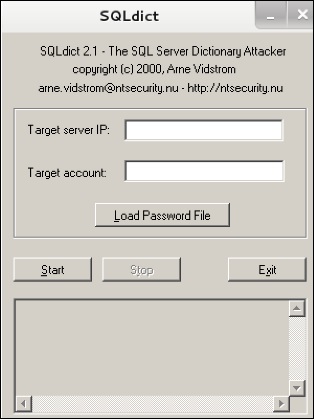
In “Target IP Server”, type the IP of the server that contains the SQL. Under “Target account”, enter the username. Then upload the file with the password and click “start” until it finishes.
hash-identifier
is
a tool that is used to identify types of hashes, that is, what they are being used for. For example, if I have a HASH, you can tell me if it’s a Linux or Windows HASH.
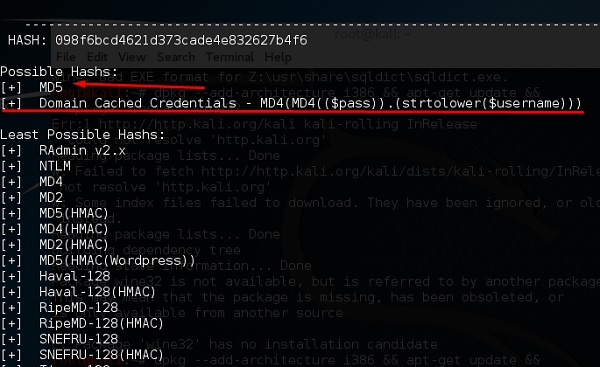
The above screen shows that it may be an MD5 hash and looks like a cached domain credential.

